How to Identify and Mitigate the Impact of the Sunburst Hack
 Sunburst Attack Overview
Sunburst Attack Overview
On December 13th, 2020 the world became publicly aware of a sophisticated and ongoing cyberattack, classified by CISA (Cyber Infrastructure Security Agency) as an Advanced Persistent Threat (APT).
Through innovative and nefarious means, the malicious actors – later dubbed UNC2452 – infiltrated the SolarWinds Orion Platform – used as an IT management and monitoring SaaS – and deployed malware which concealed itself in the .dll file, masquerading as a legitimate, signed file within the Orion Improvement Program (OIP) software. This allowed for unfettered navigation of the victim network by leveraging the OIP protocol and access assigned thereto and enabled the attackers to operate in a conventional Command & Control (C&C) fashion, running jobs, performing tasks, transferring and executing files, profiling systems, rebooting machines, and – shrewdly – disabling system services, including anti-malware applications. This allowed UNC2452 to remain largely undetected since at least the spring of 2020.
Once the attackers disabled security programs, they were free to assign administrative level privileges within the victim environment and continue to exploit the permissions to gain access to sensitive data contained within connected servers and exfiltrate it undetected at their discretion.
 Impact of the Sunburst Attack
Impact of the Sunburst Attack
Multiple U.S. Government agencies and contractors were affected and their data compromised from this attack. The full extent of the intrusion is still being investigated and uncovered as of this writing. The evasiveness of this predation is relatively unprecedented.
By adding a malicious version of the binary solarwinds.orion.core.businesslayer.dll into the SolarWinds software lifecycle, which was then signed by a legitimate SolarWinds code signing certificate, it empowered UNC2452 to remain concealed for months.
SolarWinds Orion typically uses a significant number of highly privileged accounts to perform normal business functions. Successful compromise of one of these systems can therefore enable further action. According to the CISA advisory, the following SolarWinds Orion products were impacted:
- Orion Platform 2019.4 HF5, version 2019.4.5200.9083
- Orion Platform 2020.2 RC1, version 2020.2.100.12219 SUNBURST
- Orion Platform 2020.2 RC2, version 2020.2.5200.12394
- Orion Platform 2020.2, 2020.2 HF1, version 2020.2.5300.12432
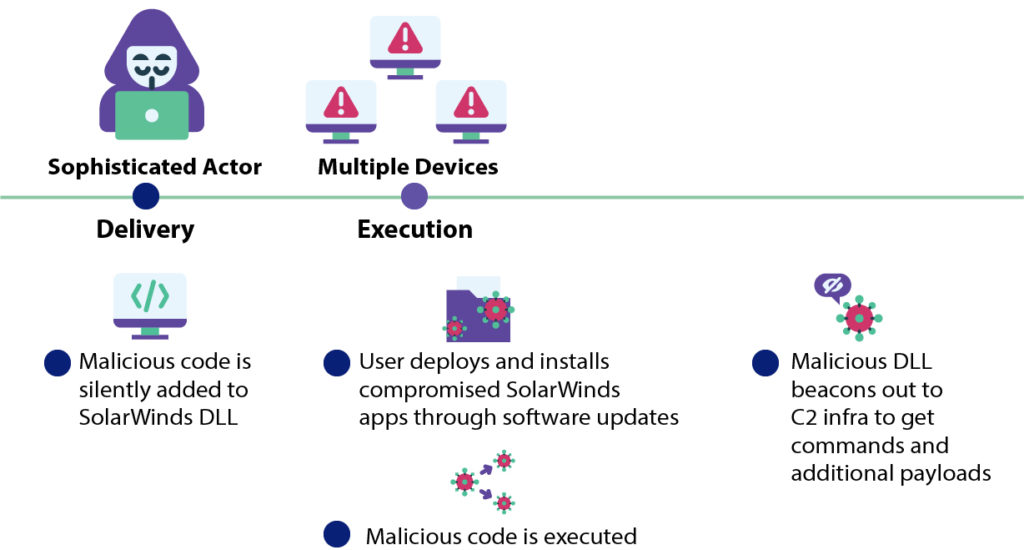
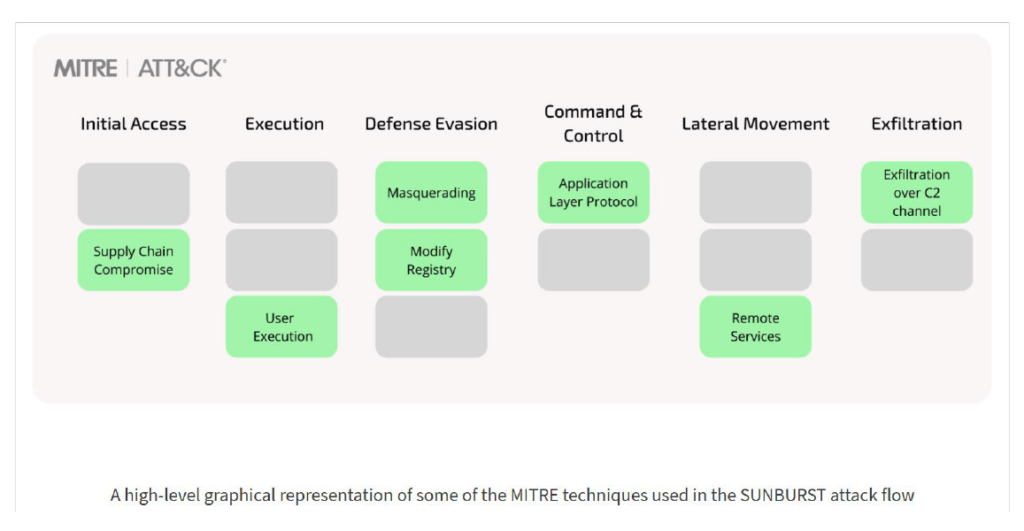
 Based on MITRE ATT&CK Framework here is the Sunburst Attack Flow
Based on MITRE ATT&CK Framework here is the Sunburst Attack Flow
By infiltrating and infecting the SolarWinds software update application, UNC2452 leveraged a supply chain attack to infect all networks and systems downloading the subsequent updates and facilitating lateral movement within the network. The attack flow is as follows:
Initial Access
The Initial Access for the malware is conducted by a Supply Chain Compromise, via a malicious DLL file that the actor successfully installs in a SolarWinds update package.
Execution
When the package is executed, the DLL is executed and the machine gets infected. The main capabilities of the malware include: Awareness activity and Execution capabilities, as well as Scripting capabilities like PowerShell.
Defense Evasion
The malware enumerates the host for the existence of specific drivers, services and processes. These are mostly security controls used by organizations, or tools used by security researchers. If any entries in the list are found, the malware will terminate and will halt any further execution. Additionally, the malware attempts to disable specific security controls detected on the host by modifying registry key settings.
Command and Control
After a dormant period of up to two weeks, the malware communicates to a Command and Control server, using a SolarWinds legitimate Application Layer Protocol, which also serves for Defense Evasion. Other Defense Evasion techniques used by the actor are impersonating legitimate entities from the network, as well as evading known endpoint security components.
Lateral Movement
The actor later uses various techniques, such as creating new tasks on remote machines using PowerShell, for lateral movement to points of interest.
Exfiltration
The attack ends in the Exfiltration of relevant data, such as emails via PowerShell email commands, or password-protected archives containing sensitive data from the victim’s servers, via standard HTTP requests.
 Are You Compromised?
Are You Compromised?
The SolarWinds attack has so far been claimed to have started in June 2020 or even earlier. It is recommended to perform a comprehensive IOC sweep across all hosts in the network, as well as examine for any abnormal federation trusts in your Azure tenants or any signs of administrative actions from unmonitored endpoints. Use SIEM tools such as Splunk Enterprise or Elastic Stack to search through the logs for an indication of anomalous activity or indicators of compromise.
 What’s Next?
What’s Next?
So, what’s your plan? You’ve detected an infection, what do you do now?
There recommended course of action is then:
- Ensure that SolarWinds servers are isolated or at least contained until a further review and investigation are conducted. This should include blocking all Internet access from SolarWinds servers.
If SolarWinds infrastructure is not isolated, consider taking the following steps:
- Restrict the scope of connectivity to endpoints from SolarWinds servers, especially those that would be are high priority assets.
- Restrict the scope of accounts that have local administrator privileged on SolarWinds servers.
- Block Internet egress from servers or other endpoints with SolarWinds software.
- Change all passwords that are affiliated with SolarWinds servers.
 And then?
And then?
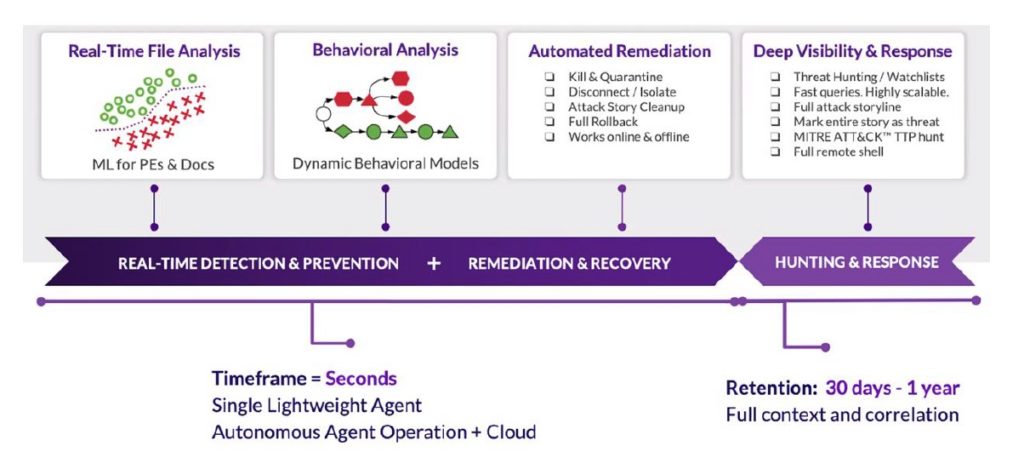
It’s time to deploy an AI-Based endpoint protection solution. You can utilize the assessment tool from SentinelOne to identify if/which SUBURST variant may have penetrated your network. SentinelOne provides a complete endpoint solution in one platform that delivers these high-level capabilities:
- Prevention: Delivered using pre-execution Static AI technologies that replace signatures. Removes the reliance on known signatures and constantly updating databases.
- Detection: Delivered using on-execution Behavioral AI technologies that detect anomalous actions in real-time, at the endpoint, without cloud reliance. Used to detect fileless attacks, exploits, bad macros, evil scripts, cryptominers, ransomware, and other attacks.
- Response: Delivered in milliseconds to shutdown attacks thereby reducing dwell time to near zero. Includes alert, kill, quarantine, and network containment.
- Recovery: One-click reversal (remediation) of unwanted changes, Windows rollback to recover data. A full remote shell to interact with endpoints using a command-line interface available across Windows, macOS, Linux, and containers.
- Hunting: Delivered as a supplement to Prevention/Detection/Response for organizations that need advanced Indicator of Compromise (IoC) and artifact hunting capability.
 Moving Forward
Moving Forward
There are innumerable prospective applications to consider deploying going forward to redouble network integrity efforts and ensure the infection has been rooted out. Some of these are more robust and integrated than others.
SentinelOne – Deep Visibility:
A rapid hunting tool that imparts storyline technology, effectively building a model of an endpoint infrastructures operating behavior. It consolidates similar processes and assigns a Storyline ID, which allows for anomalous events to be identified quickly, how they began, and how far they’ve spread.
BeyondTrust:
BeyondTrust Privileged Remote Access solution can be used for managing and auditing internal and third-party remote privileged access, without the need for a VPN. The solution also features strong monitoring capabilities, with tracking and auditing capabilities all accessible in a single interface.
GAI HyperCAP (Hyper Converged Analytics Platform)
HyperCAP is a validated and integrated end-to-end cyber analytics solution. Using the GAI HyperCAP solution, agencies can combine, integrate and correlate Network, Email, Content, and Endpoint Security data and indicators of compromise from several other sources including meta-data, malware events, and data on known and new threats, especially the one arising from SUNBURST. GAI HyperCAP provides analytics around cyber threat detection and remediation use cases. The solution can be used to ingest data from various security controls and visualize threats across multiple parameters, investigate cyber security alerts, and see threat trends using dashboards and reports.
 The Opportunity
The Opportunity
As the pervasiveness and degree of sophistication with these attacks intensifies, corporations are in critical need of Security Analysts trained and certified in the most up-to-the-minute threat detection and remediation techniques so that they can build proactive models to forestall future successful attacks. Or to swiftly identify, address, and contain any infections before sensitive data is compromised.
How can I do that? There are a handful of well-established institutions that provide comprehensive, training and certification pathways At Intellectual Point, we provide truly cutting-edge, hands-on training in real-world environments to prepare our students to quickly assume essential roles within their organizations, providing critical security and support. We offer more than 80 programs with an emphasis on advanced, enhanced security training to meet an insatiable demand for qualified, highly skilled talent in the workforce.
We provide intensive education in CompTIA Security+ certifications, Amazon Web Services Solution Architect, a Certified Ethical Hacker, and Cisco Certified Network Analyst (CCNA). And, due to our innovation and agility, we are now able to offer all of our instructor-led courses virtually, expanding our footprint to the entire North American population.
The average Network Security System Analyst in the Washington, D.C. metro area is earning $98,425 annually. With a variety of learning paths that prepare students to instantly make a positive impact with their employers, we’re positioned to empower you to complete advanced certification training in 144 hours. The first-year ROI can be more than 200 times your initial investment.
If you’re interested in being part of the interconnected team of global experts committed to predicting and preventing attacks like the Sunburst APT, visit https://www.intellectualpoint.com/it-training-intellectual-point/ to learn how to transform your career prospects from uninteresting to unimaginable.
What to Learn More?
Join our Free Digital Natives Meetup that will talk about the Sunburst Hack!
February 18, 2021, at 6 PM



































Leave a Reply
You must be logged in to post a comment.