Understanding Threat Actors 101
It is important to have a strong and robust defense. The success of your defense relies on understanding your enemy. Who is your enemy and what are their motivations and goals? In cybersecurity, this ‘enemy” is called the threat actor. A threat actor can be a person, group, or entity that creates all or part of an incident with the goal to impact security. To create a secure cybersecurity plan you need to be aware of their motivations as well.
Types of Threat Actors
Government-Sponsored/State-Sponsored Actors. These threat actors are funded, directed, or sponsored by nations. They’ve been known to steal and exfiltrate intellectual property, sensitive information, and even funds to further their nation’s espionage causes. They are typically motivated by political, economic, technical, or military agendas. They are often looking for competitive information, resources, or users that can be exploited for espionage purposes.
Chief Goal: Espionage, theft, or any other activity that furthers the interests of a particular nation/group of nations.
Typical Targets: Businesses and Government-run Organizations.
Organized Crime/Cybercriminals. Crime is everywhere, and the internet is no different. Criminals who want to steal sensitive data, money, and personal information are out there. However, since they’re after financial gain, the data they take does tend to show up on the black market or is sold to the highest bidder. These threat actors are also known to use ransomware to extort business owners directly. They are typically either looking for personally identifiable information (PII) of your customers or employees, such as social security numbers, health records, credit cards, and banking information or to hijack and ransom critical digital resources.
Chief Goal: Financial Gain.
Typical Targets: Cash and/or Data-Rich Organizations and Businesses.
Hacktivists. Hacktivists focus on bringing awareness. For example, almost all the information leaked by WikiLeaks as a result of hacktivists who wanted to expose the truth. They’re usually motivated by ideological activism. These attackers have a political agenda. Their goal is to either create high-profile attacks that help them distribute propaganda, or to cause damage to organizations they are opposed to. The ultimate goal is to find a way to benefit their cause or gain awareness of their issue.
Chief Goal: Exposing secrets and disrupting services/organizations that are perceived as evil.
Typical Targets: Not limited to any specific type of organization or business.
Insiders. Sometimes, you don’t need to look far to find infiltrators. Some threat actors can go as far as infiltrating your workforce themselves or turning an insider towards their cause/goal. Insiders are a particularly nasty threat to any organization’s cybersecurity because of the amount of access they’d have when working from within. Attackers operating inside your organization are typically disgruntled employees or ex-employees either looking for revenge or some type of financial gain. They sometimes collaborate with other threat actors, such as organized crime or government-sponsored hackers, out of a sense of loyalty, or in exchange for money or prestige.
Chief Goal: Work from within an organization to get around its cybersecurity framework.
Typical Targets: Not limited to any specific type of organization.
Script Kiddies. Some attackers aren’t skilled/advanced enough to design penetration tools on their own. Script Kiddies use tools developed by other attackers to penetrate a network or system. These attackers are usually amateur criminals, often referred to as script kiddies, who are driven by the desire for notoriety. Sometimes, however, they can legitimate security researchers trying to help organizations find and close security vulnerabilities, or even professional hackers (sometimes known as gray hat hackers) looking to profit from finding and exposing flaws and exploits in network systems and devices.
Chief Goal: Attack computer systems and networks, vandalize, and inflict as much damage as possible.
Typical Targets: Easy-to-penetrate systems, which are vulnerable to widely-known threats.
Internal User Errors. Not all threat actors are malicious. But the damage they do cause can be quite extensive. Even simple user errors can end in catastrophe because of their elevated permissions within an organization’s systems and networks. Users making mistakes with configurations are actually the largest threat organizations face. These threat actors exist largely due to failing to design flaws out of the network, or by providing privileges to individuals who should not have them. Internal user errors have been known to bring down critical resources such as firewalls, routers, and servers, causing widespread or departmental company outages.
Chief Goal: Not malicious, often inadvertent.
Typical Targets: Can affect any organization, however secure.

Common Threat Actor Motivations
Understanding threat actors and their motivations is an essential step in the cybersecurity process. It will help you map out your defenses and may help you better outmaneuver attackers successfully.
- Political, Economic, Technical, and Military Agendas
- Profits/Financial Gain
- Notoriety
- Revenge
- Overlap of Motivations
Types of Threat Intelligence
Threat Intelligence (TI) is any external information about a threat that an organization can consume and integrate into its defensive decision-making process that results in something actionable, such as a new policy, configuration, or design, or leads to the selection and deployment of a new device. This intelligence can be Strategic, Tactical, or Operational.
Types of TI:
- Strategic – Printed or online reports that focus on threat actors, their intentions, motivations, capabilities, and plans. This information is usually used by CISOs and IT management to determine what type of additional administrative, physical, or technology concerns many need to be budgeted or planned for.
- Tactical – Focus on understanding the tactics, techniques, and procedures of threat actors. “How are they accomplishing their cyber mission?” Security and network operation teams use this intelligence to understand and prioritize vulnerabilities, establish alert escalations, and inform design considerations and configuration changes in order to design flaws and vulnerabilities out of the network itself.
- Operational – Relates to specific attacks or campaigns. It helps defenders understand the nature, intent, and timing of a specific attack, and also provides insight into the nature and sophistication of the group(s) responsible.
Threat Modeling Methodologies
Threat modeling is a proactive strategy for evaluating risks. It involves identifying potential threats and developing tests or procedures to detect and respond to those threats. This involves understanding how threats may impact systems, classifying threats, and applying the appropriate countermeasures.
- Reconnaissance: In this phase, the attacker needs to understand as much as they can about your organization and network.
- Weaponize: This is the phase where the attackers will build malicious code to exploit identified vulnerabilities within the target, and also ensure that the exploit goes undetected.
- Delivery: Now that the attacker has chosen their cyber weapon, they have to figure out the best mechanism to deliver it. As most of us know, the delivery vehicles of choice are social engineering and phishing emails.
- Exploit/Execute: Once the exploit is delivered it needs to be executed without being detected.
- Command & Control: Once the vulnerability has been successfully executed, the first thing it does is try to communicate undetected back to its owner or server in order to download malware and other tools for further compromise.
- Internal Reconnaissance: Since the first insertion point is usually a vulnerable workstation, attackers need to move laterally through the network in order to map the infrastructure and to find the data they are looking for to complete their cyber mission.
- Maintain: Now that the attackers are in, they want to stay as long as possible.

What Comes Next?
No matter where you start, all cybersecurity careers begin with general IT experience. You need to understand how the technology works before you can learn how to secure and protect it.
What Cybersecurity Career Path are you on?
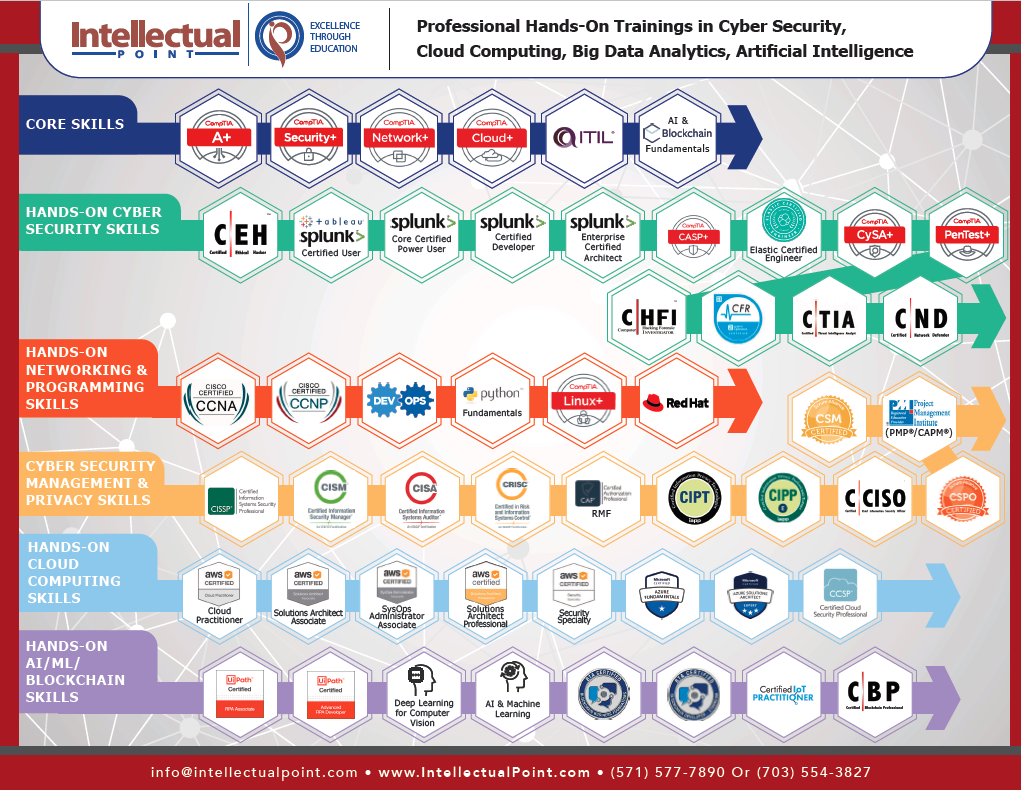
How to get started in an IT Career with Intellectual Point
—




































Leave a Reply
You must be logged in to post a comment.